How Do Tech Giants Compare at Protecting Privacy?

When it comes down to it, which major Tech companies have your back?
It’s hard to tell who is prioritizing protecting the privacy of users and which companies just seem like they are.
Brace yourself for a surprisingly in-depth look at where the Tech giants you partner with rank when it comes to protecting the privacy of your online info from external surveillance.
And before you make the old, “Well, I have nothing to hide,” argument, consider the WannaCry and Adylkuzz global cyberattacks.
The perpetrators hacked the NSA and used their tools to commit cyberattacks, meaning they might also be able to hack into NSA’s files on U.S. users’ online info and data.
Everything you need to know about tech corporation privacy protection rankings:
- The truth about cybersecurity and protecting privacy
- Tech corporation privacy protection policy rankings
- Why do privacy policies matter?
- How to improve your privacy protection policy
- Top three in-demand cybersecurity roles
The truth about cybersecurity and protecting privacy
Let’s get the contextual (Read: boring) facts out of the way first.
Earlier this week, the Electronic Frontier Foundation (EFF) released its seventh annual “Who Has Your Back” report.
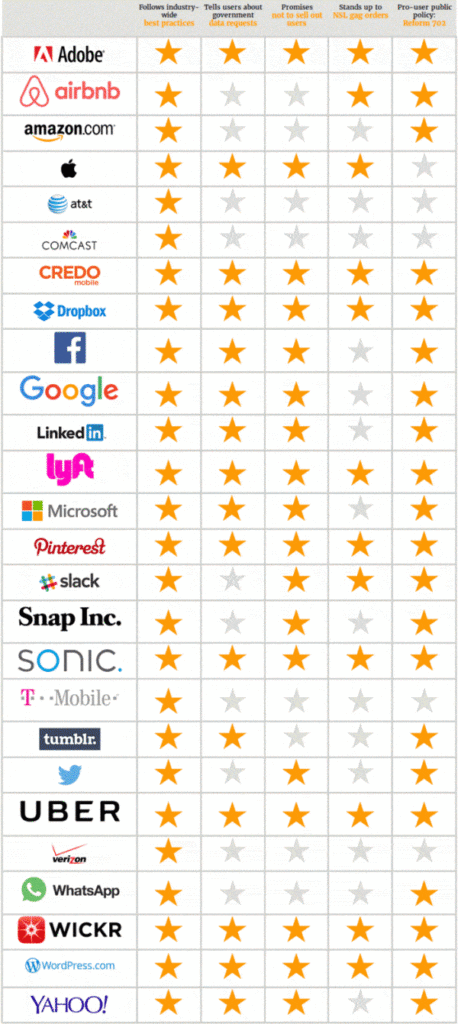
The report evaluated 26 Tech giants on how well they are protecting the privacy of their users from external and government surveillance.
They based the rankings on five components which translate to the 5-star ranking system: if they follow best practices for privacy, if they inform users when the government requests data, if they promised not to sell users’ data, if they took a stand against gag orders, and if they are pro-reforming the NSA’s Section 107 program. (Not familiar with that last one? Neither were we. Learn about it here.)
Tech corporation privacy protection policy rankings
The privacy protection rankings include 26 companies like Uber, Adobe, Google, Twitter, and WhatsApp and are based on a 1-5 star system with 1 being the worst and 5 being the best.
5-star privacy protection policy tech companies
Now that those details are out of the way let’s get to what matters: the rankings. Out of the 26 companies listed, only nine received 5-star rankings for meeting all five criteria, which included Adobe, Credo, Dropbox, Lyft, Pinterest, Sonic, Uber, Wickr, and WordPress.
As a company that uses WordPress, Adobe, Uber, and Lyft for various business needs we were relieved to see them on the top of these privacy protection rankings.
4-star privacy protection policy tech companies
Google, Microsoft, Facebook, and LinkedIn all lost a star for abiding by NSL gag orders, and Apple got docked one star for the company’s stance on the NSA’s Section 702.
3-star privacy protection policy tech companies
Twitter, Snap, Tumblr, and Airbnb ranked lower with only three stars.
2-star privacy protection policy tech companies
While WhatsApp and Amazon, the most surprising low-ranking Tech giant listed, nabbed only two stars each.
1-star privacy protection policy tech companies
What came as no surprise was the one-star rankings for all major phone carriers on the list, including T-Mobile, Verizon, and AT&T considering their embattled history with protecting privacy by providing external sources with the data they need to inform things like highly targeted Digital Marketing campaigns or investigations.
Although it’s unsurprising the low rankings of Verizon and AT&T, businesses and private U.S. citizens alike rely on these major telecommunication providers for primary communications and Internet connectivity which makes their susceptibility to governmental and external overreach even more troublesome for companies that do business using these services.
Complete list of privacy protection rankings provided by the EFF report:
Why do privacy policies matter?
These stats matter because it involves your most valuable asset: user data.
While an external source is likely requesting or purchasing the info for valid or understandable reasons like gathering evidence for an investigation or merely creating more targeted marketing campaigns, the problem is that the data then becomes less secure.
More access to private data and online info on individuals or businesses means higher chances of a successful cyberattack.
Cyberattacks are already a concern for businesses with user data under their own roofs or with the outside vendors they partner with for business needs like Amazon’s Web Services or telecommunication through Slack.
However, by providing external sources with online user data and information, Tech companies are widening the scope of accessibility to this data, thus making successful cyberattacks more likely.
But there’s hope.
How to improve your privacy protection policy
There are several ways to improve your privacy policy to protect user data that include evaluating your current policies, hiring cybersecurity talent like cybersecurity engineers, and determining which tech providers are in line with your policies.
Evaluate your current tech providers’ privacy policies
First, evaluate which Tech companies’ services your business uses.
Is it critical to the function of your business? Is there another Tech company listed ranking higher for protecting privacy you could transition to without sacrificing quality or results?
The cybersecurity professionals at your company are best equipped to answer these questions and develop the most effective cybersecurity and privacy protection strategies for when external user data requests are received or when cyber threats are detected.
Hire cybersecurity talent to improve your privacy protection
Hire the cybersecurity talent you need to ensure your sensitive data and online information is protected from all types of threats, including external, U.S.-based sources.
Privacy protection and cybersecurity are connected threats. Tech experts skilled in cybersecurity are aware of the privacy lapses highlighted by the EFF’s report and their assistance will help mitigate cyber threats and identify potentially unsecured data requests effectively.
Top three in-demand cybersecurity roles
The top three in-demand cybersecurity roles that companies are hiring right now to improve their privacy protection and user data are cybersecurity engineers, security architects, and incident security responders.
Hire Cybersecurity Engineers
These Engineers build your cybersecurity system. Typically working under a Security Architect or Cybersecurity Manager, they work to develop the most effective solutions for your cybersecurity needs.
Hire Security Architects
Security architects are typically a senior position that involves leading an IT team along with designing, building, and overseeing complex network and computer security at a high level. This is commonly a role large enterprise businesses prioritize hiring for.
Hire Incident Security Responders
These pros deal with post-hack damage. They know how to investigate cybersecurity hacks effectively and identify the weak points where hackers were able to breach the system to prevent any successful future attacks.
Tech giants and protecting privacy
Cyberattacks from both international and U.S.-based sources are a primary concern for Tech companies like ourselves and non-Tech businesses as well since data is a core asset for modern businesses across all industries.
The Tech industry as a whole has moved toward more transparency when it comes to protecting privacy of users, but some are moving much slower than others.
Use the rankings found here to determine which Tech providers are the most secure option for your business needs and hire the cybersecurity experts needed to keep your data and private online information protected.
If you lack the roles highlighted above or are looking to expand your IT or cybersecurity teams, contact Mondo today. We have the high-end talent you need to keep your data safe in the ever-evolving environment of online privacy protection.
Looking to hire top-tier Tech, Digital Marketing, or Creative Talent? We can help.
Every year, Mondo helps to fill over 2,000 open positions nationwide.
More articles about job searching and industry trends:
- Top 3 Employee Retention Strategies for Tech Workers
- The Benefits of Hiring Faster: Why Speed is Crucial
- The Top 5 Reasons We Need More Women in Tech
- Returnship Programs: Reentering the Workforce After an Employment Gap
- How to Best Explain Having a ‘Gap’ on Your Resume
- Ways to Spot Bad Boss Characteristics & Behaviors in an Interview
- 6 Most In-Demand Tech Skills to Get a Job in 2023
- What Does a Recruiter Do & Who Do They Work For?